Network security
The DotAlign Cloud app uses Azure Active Directory for authentication and authorization. If you're using an identity provider like Okta along with Azure AD, it will be automatically used during the authentication flow. Azure AD is a best in class identity provider service and using it ensures that DotAlign Cloud is using the most up to date information from your company's directory.
Apart from Azure AD, your DotAlign Cloud deployment also benefits from many of security features available in Microsoft Azure. These include features at the resource level such as data encryption and IP address based allow/disallow rules, and also networking related features like VNETs and private endpoints.
If you've chosen to enable traffic restrictions and private endpoints while deploying DotAlign Cloud, this is what the architecture will be like.
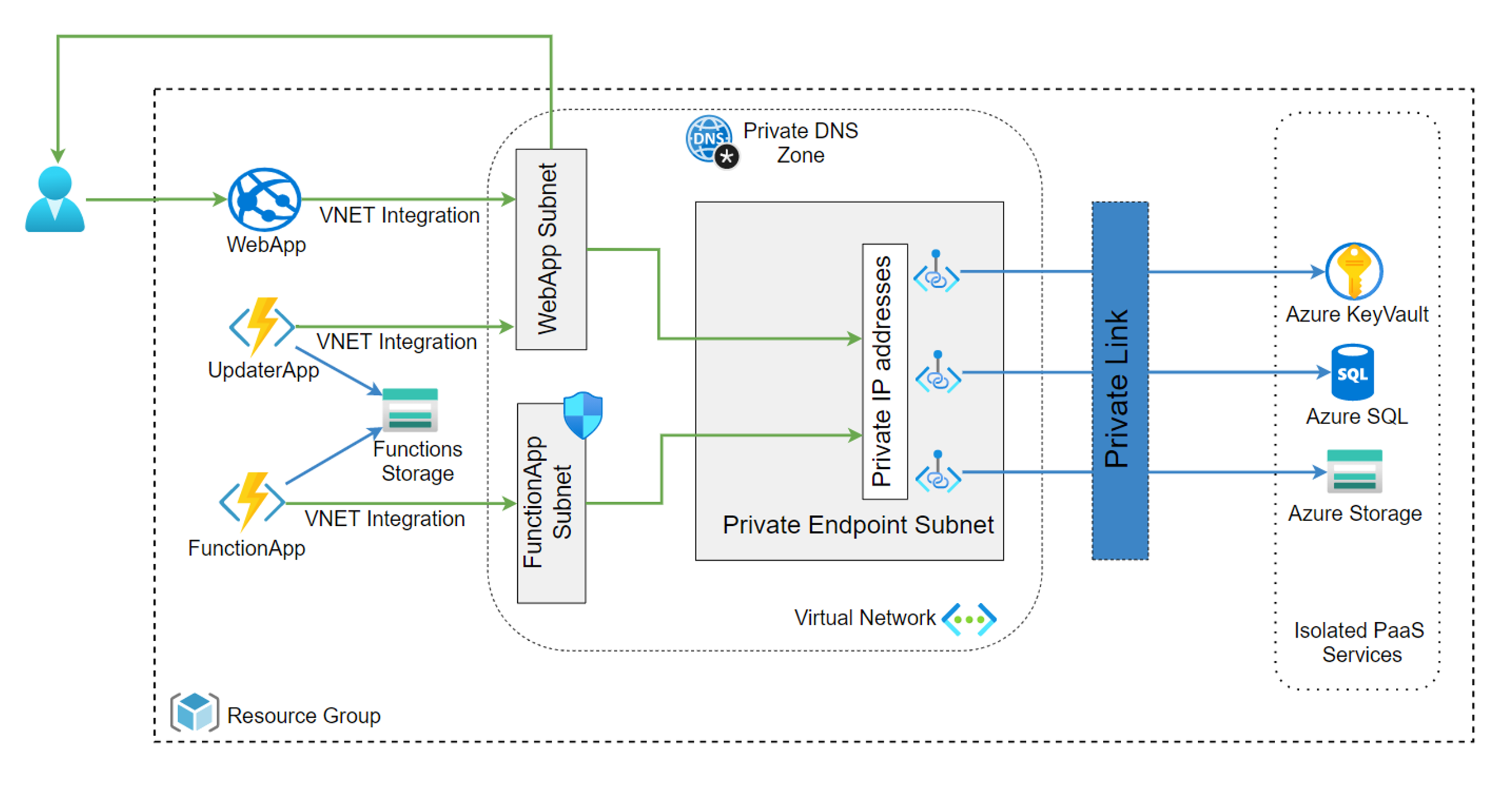
Note that all the resources are a part of a VNET and the database and key vault are only accessible via the private endpoint subnet. There are also outbound IP restrictions on the function app, which ensure that any outbound access is only to IP addresses explicitly allowed.
Setting up restrictions on the web app
By default, as long as the user can authenticate and has authorization, your DotAlign Cloud web app is accessible from any IP address, as that allows for flexibility of access (including from mobile devices). If you would like to lock it down to a specific set of IP addresses, you can easily do so from within the Azure portal.
To do this, please follow these steps:
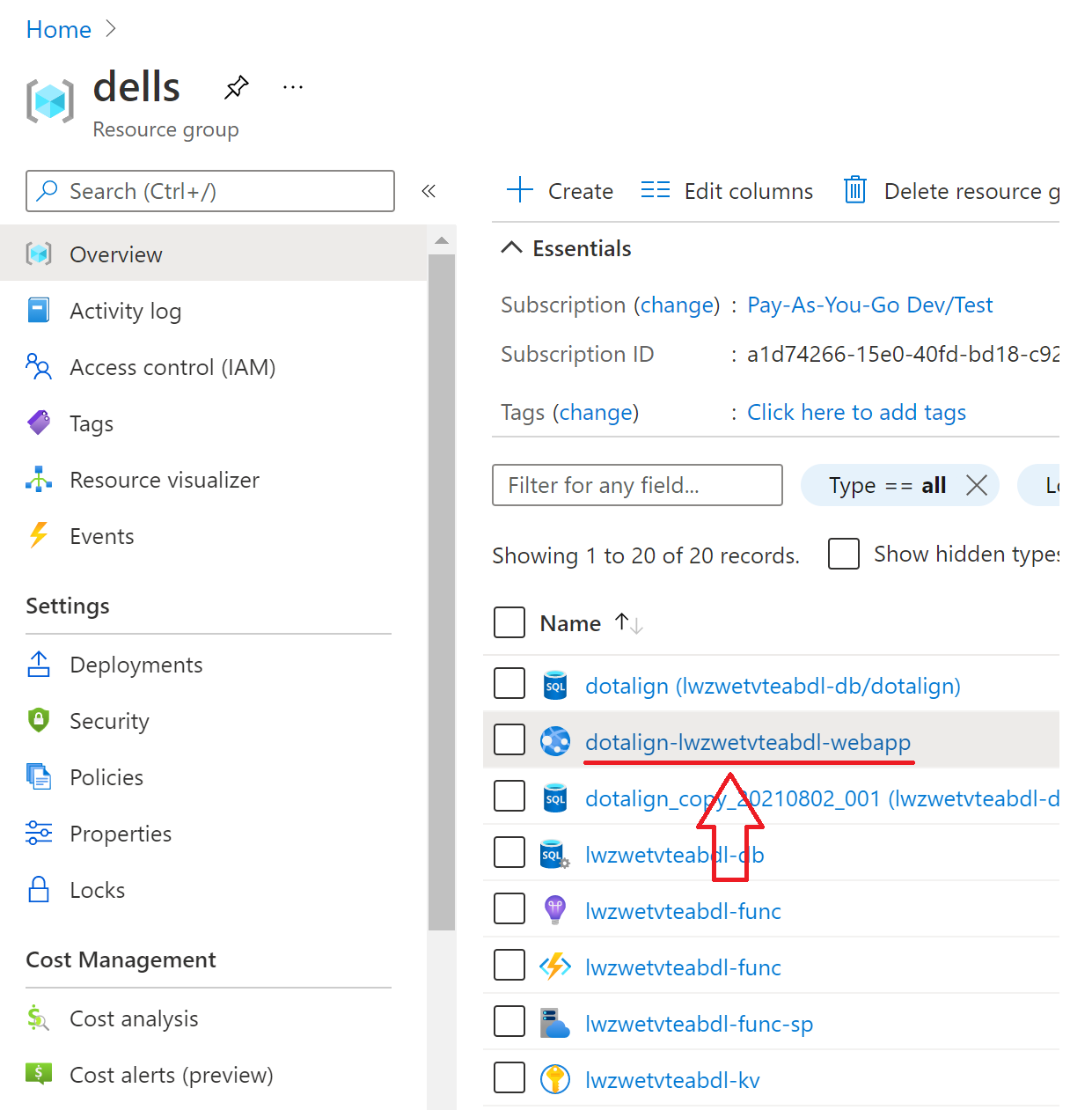
- Go to the resource group where DotAlign Cloud is deployed, and click on the web app. Its name is in the format
dotalign-UNIQUE_ID-webapp
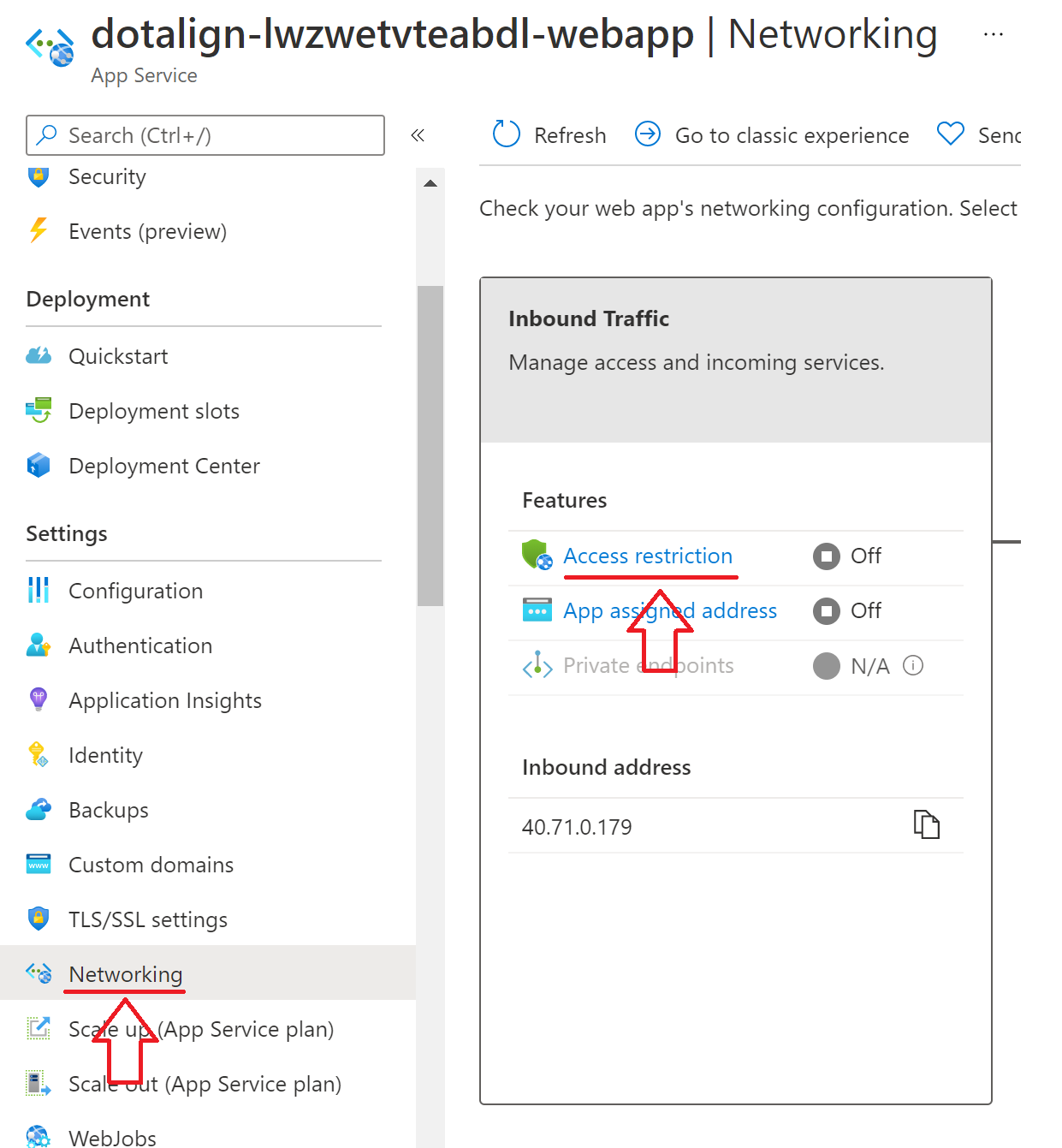
- When looking at the web app, go to the networking section, and then click on "Access restrictions".
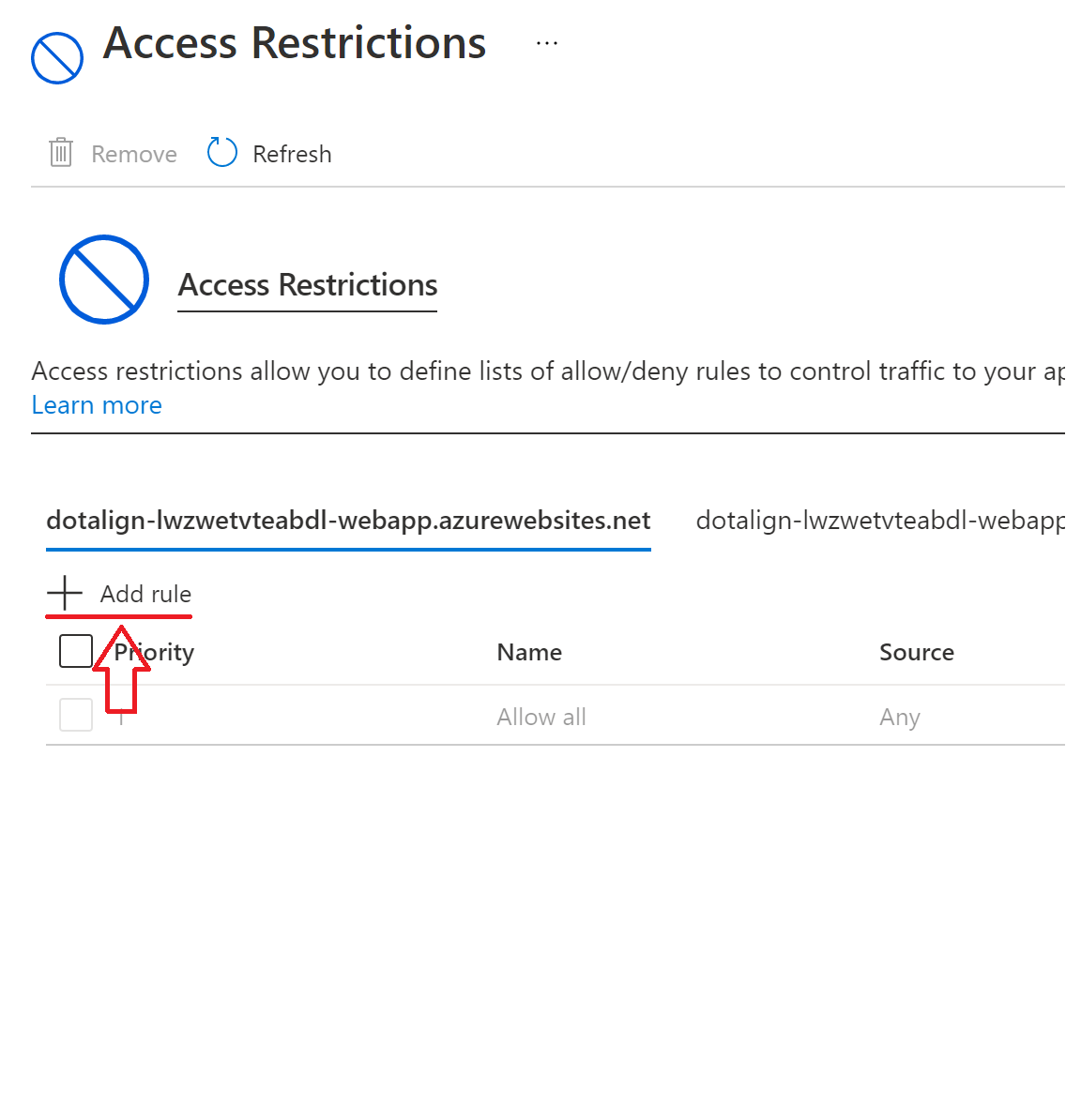
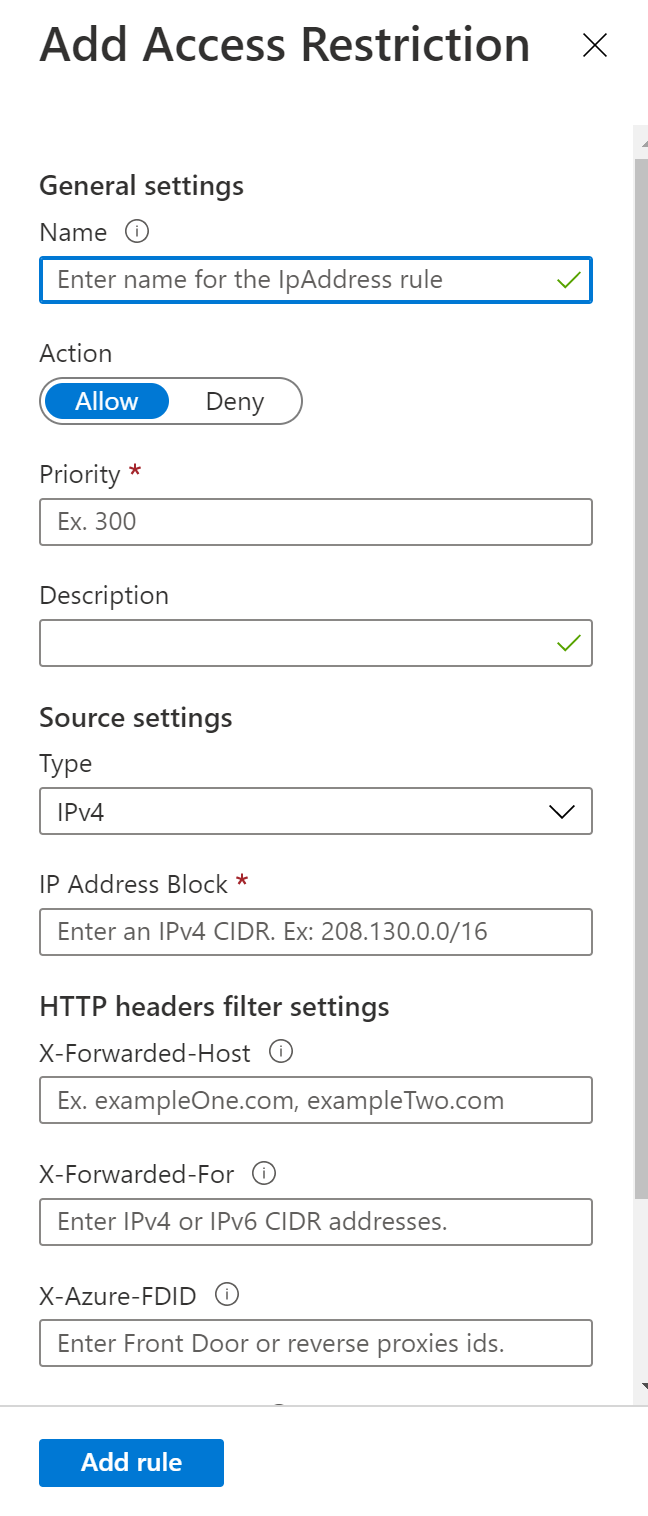
- Here you will see the access restrictions that have been set up for the web app and you can also set up new ones. Click on the "Add rule" button to create a new one.
- Fill in the details pertaining to the rule you would like to add and click on "Add rule" to apply. You can find detailed documentation about how to set up the rule here.
Relevant links
- Overview of Azure virtual networks (Vnet) - https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-overview
- Overview of Azure private endpoints - https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-overview
- Adding an access restriction to an app service - https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions

