Managed Identity based access to MS Graph
Managed identities in Azure provide a great way of not having to deal with messy credentials or certificate based authentication. They can be used to provide apps with access to resources like databases, storage accounts and thankfully, the MS Graph API!
To set up managed identity based access to the MS Graph API for your app, you must have the following pieces of info.
The Object Id of the Graph API resource on your Azure tenant
You can obtain this by looking for the well known ID of the MS Graph API, which is "00000003-0000-0000-c000-000000000000", inside your Azure portal UI.
When I search for that ID, I find a service principal called "Microsoft Graph" show up inside the Microsoft Entra ID section.
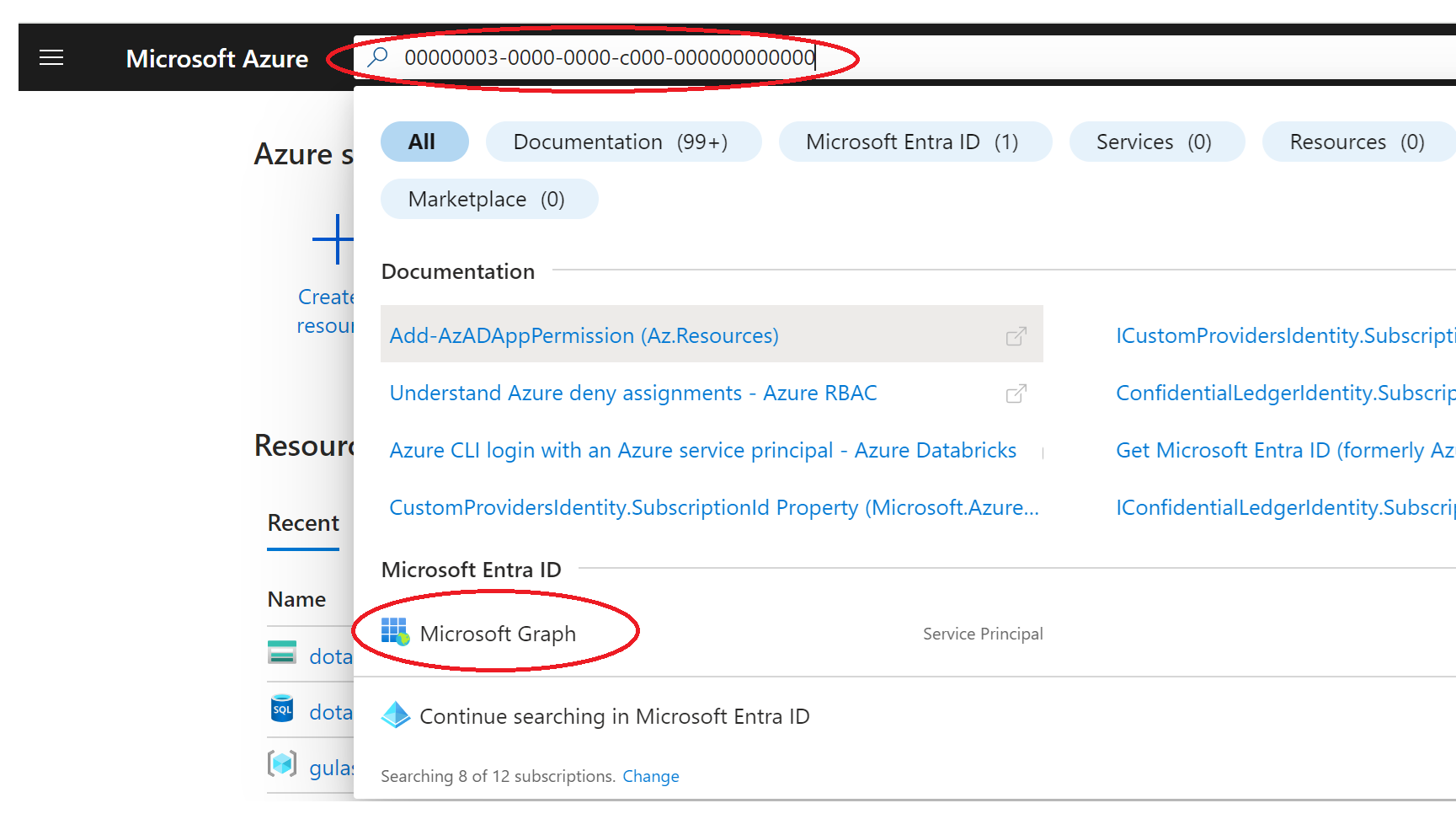
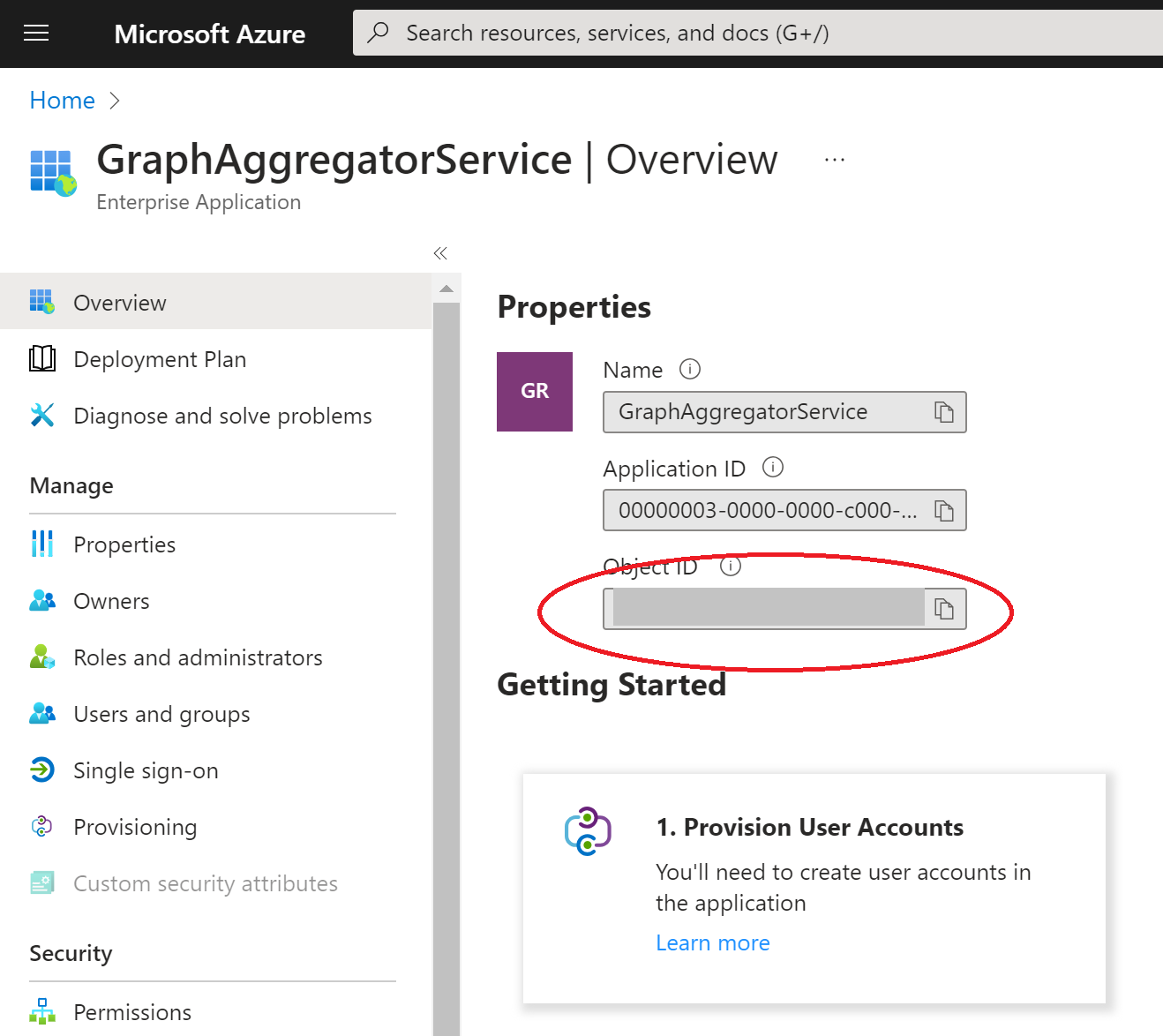
On clicking into it, you will see the details of the service principal, including the name (typically GraphAggregatorService) and the Object Id assigned to it inside your Azure tenant (hidden here for security reasons).
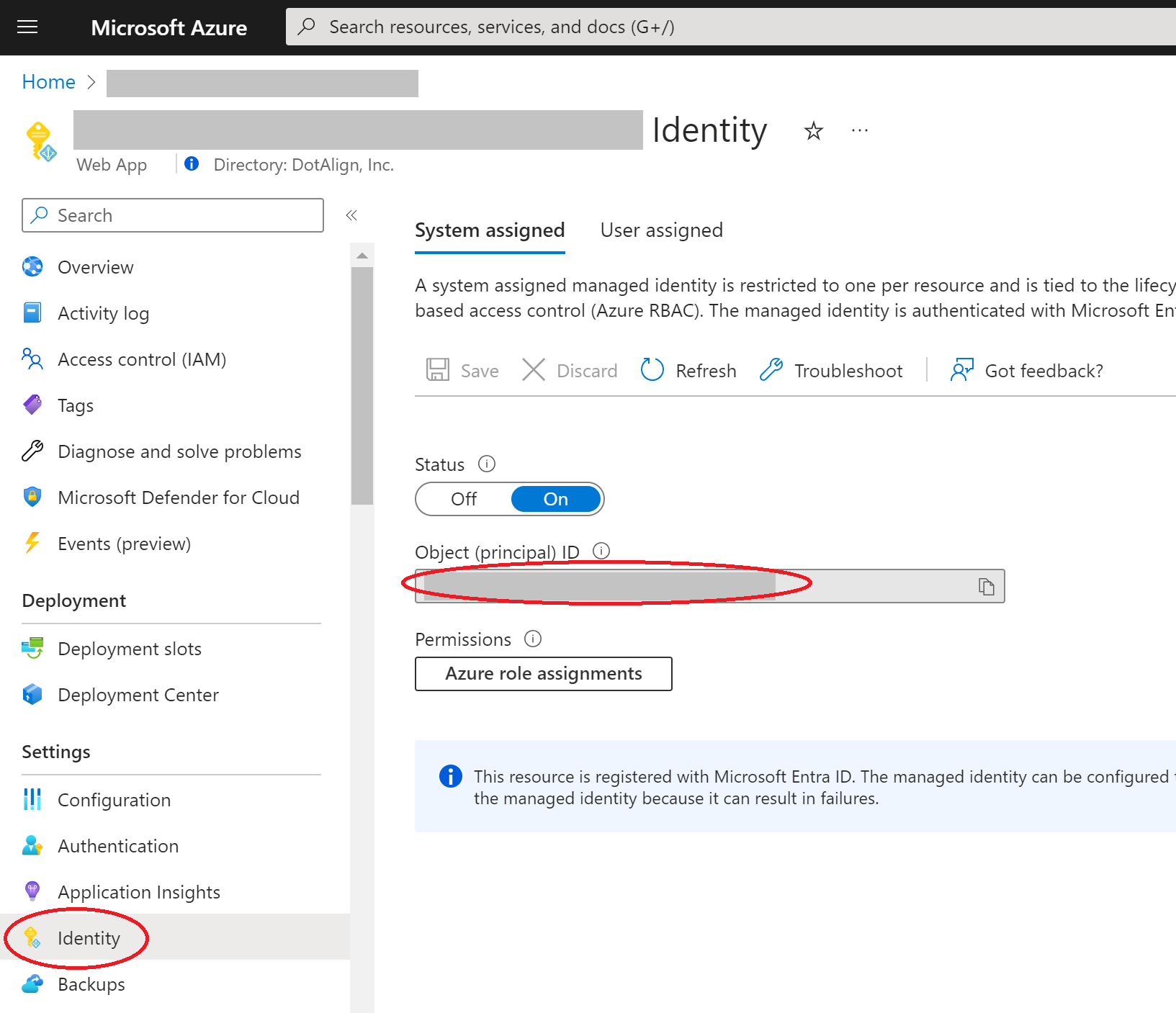
The managed identity of your app
You can find the the Object ID of your app's managed identity by going into the identity section of your app inside the Azure portal. If you have not already turned on managed identity, you can from this screen, and then you will be able to see and copy the Object ID.
The scopes (or permissions) you would like to provide your app access to
The IDs of the available MS Graph scopes are document in the link below:
https://learn.microsoft.com/en-us/graph/permissions-reference
For example, if you were interested in providing the Directory.Read.All scope with "Application" type (i.e., without requiring a signed in user), you would use the ID of 7ab1d382-f21e-4acd-a863-ba3e13f7da61.

